Stridon: How law firms can counter the risk of cybercrime
The risk of cybercrime
Data security should be a top priority for any legal practice. Clients trust law firms with their most sensitive and confidential information. Plus, law firms have an ethical, professional, and legal duty of care to protect client data against unauthorised disclosure or access.
In the past year, however, the task of securing law firm data has become a significantly more complex proposition.
Cyber threats are mounting
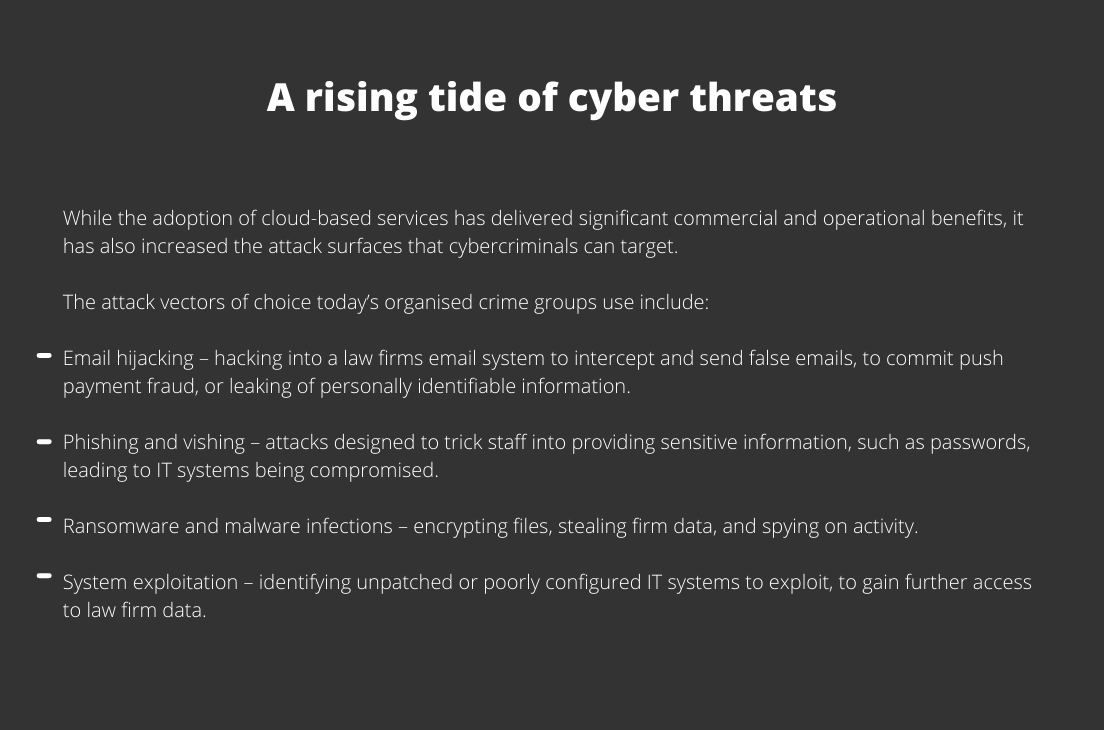
The COVID-19 crisis has had a major impact on the way legal professionals in law firms work with colleagues and clients. Over the past year new technologies and digital ways of working have exposed law firms to an escalating threat landscape.
As custodians of sensitive information and large amounts of client money, law firms are an attractive target for cybercriminals. Without having the appropriate security measures in place, law firms put their reputations – and their clients’ data and money – at risk.
With enhanced cloud services and hybrid working models on the horizon, taking a proactive stance on cyber security will be crucial for mitigating and managing risk. The time to act is now because UK law firms are operating in an increasingly hostile digital landscape – and security measures that may have been appropriate in the past will prove inadequate going forward.
Rising to the risk mitigation challenge
In recent months, law firms have become increasingly concerned about their vulnerability to cyber penetration.
The consequences arising from compromised email accounts, public leaks of privileged attorney-client data, or the inability to access information due to ransomware are significant. Breach events potentially expose law firms to malpractice and negligence lawsuits and could impact their ability to indemnify the business in the future.
Worse still, any data breach must be reported to the ICO and made public – a revelation that could prove catastrophic to a firm’s reputation. Plus, any violation of GDPR data protection laws can result in a punishing fine.
While professional indemnity insurance may cover losses resulting from a cyberattack, it is unlikely to include regulatory fines due to negligent security processes.
A commercial imperative
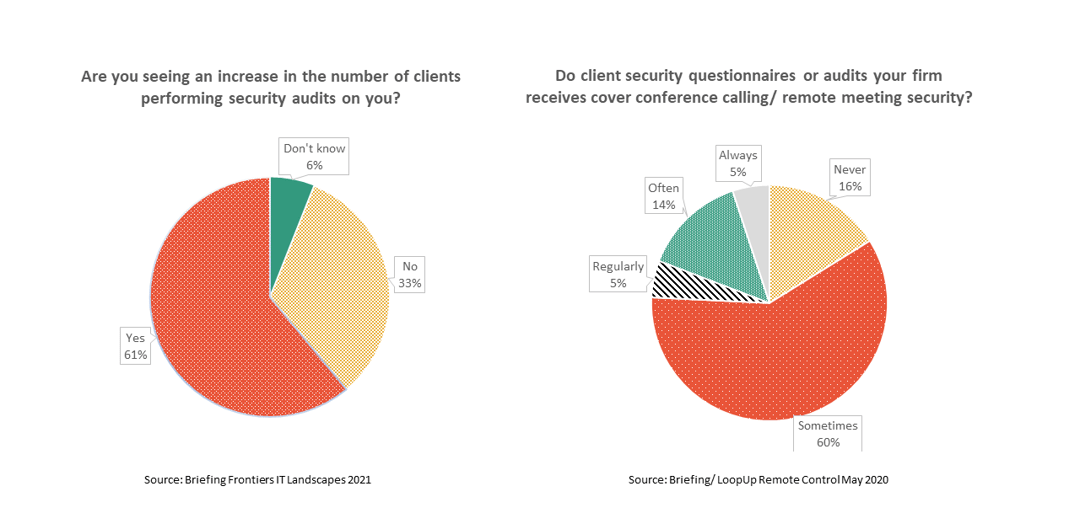
Turns out that cybersecurity isn’t just a top concern for practice partners. It’s also rising in importance for commercial clients too.

Getting Started: A Framework for Success
When it comes to reducing your risk from cyber-crime, preparation should always be the first line of defence.
But how do you address the practicalities of cybersecurity when you have so many solutions to choose from and you’re not sure where the top risks lie – or which to address first? You may also be asked by your clients – or prospective clients to provide proof that your systems have adequate and rigorous security policies in place – especially if they operate in a highly regulated industry like Finance.
The answer is to work with a framework of best practices that can be applied to your unique operating environment.
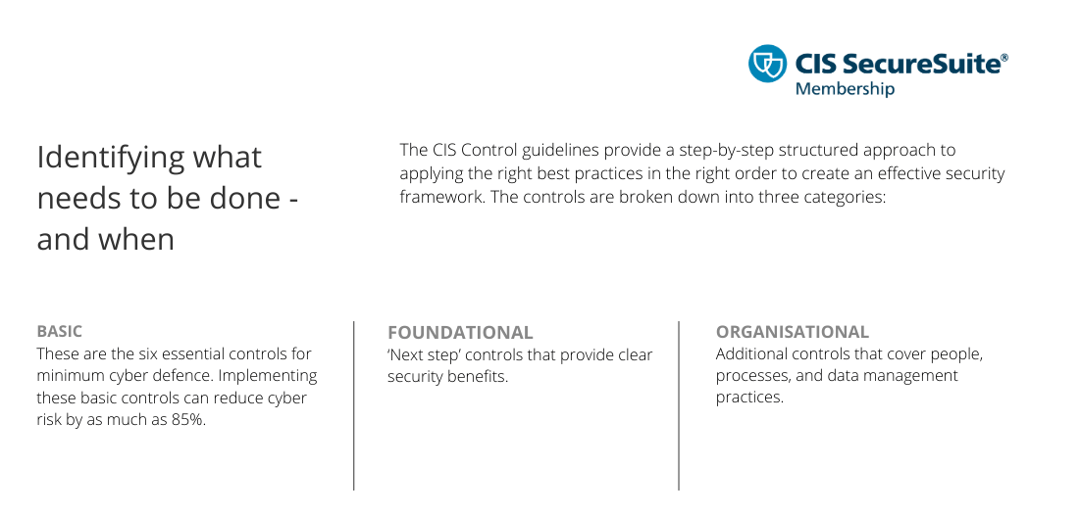
The UK’s National Cyber Security Centre’s Cyber Essentials (CE) certification is a good place to start. As well as setting out basic technical controls, it also lays the foundation for developing policies and procedures to mitigate against threats that can impact business operations. But for most law firms, the Cyber Essentials certification does not go far enough and is only recognised within the context of UK business.
So, what else is out there? The good news is, there are ranges of information security frameworks available that can be selected, based on the overall size, type, and risk posture a law firm has. The US National Institute of Standards and Technology has developed the comprehensive Cybersecurity Framework (CSF), and at the very top end, the globally recognised, externally certified ISO 27001.
Here at Stridon, we utilise the gold-standard Center for Internet Security (CIS) Controls framework to evaluate your current risk profile, identify what you need to do to improve your security posture right now and develop a roadmap for the future. CIS Controls provide the perfect jump-off point for law firms just starting to formalise their cybersecurity posture; a step up in robustness compared to Cyber Essentials, but achievable for any size of a law firm, that may otherwise struggle with the investment needed in time and funds to achieve ISO 27001 certification.
Quite simply, our goal is to ensure that you start secure – and stay secure for the long term.

The CIS Controls Methodology – a Holistic Approach
Unfortunately, many law firms don’t have adequate cybersecurity policies or protection measures in place to prevent their operations being compromised by threat actors.
The CIS Controls framework provides a prioritised set of actions that collectively form a defence-in-depth set of practices designed to mitigate the most common attacks against systems and networks.
Going way beyond the much more basic Cyber Essentials recommendations, it provides an ideal foundation for navigating the evolving complexity of the technology ecosystems today’s law firms depend upon.
As an authorised CIS partner, Stridon can help law firms assess and improve their current security state. Delivering a deep understanding of what is critical to your business, data, systems, networks, and infrastructures – and the steps you need to take to protect your IT assets and personnel.
It’s a holistic approach that encompasses every aspect of how your firm operates. Because cybersecurity has become part of doing business today, it evaluates people, technology and which available safeguards are most appropriate for your environment.
Working through the CIS framework we’ll be able to help you:
Understand your risk – undertaking an operational risk assessment, we’ll evaluate your current cyber defence maturity and your IT infrastructure and operations to identify where the vulnerabilities lie.
Identify which defensive steps provide the greatest value – prioritising which controls will provide the greatest risk reduction, so you can build an effective and practical defence.
Understand which controls can be best used to solve which problems – whether that’s detecting indicators of compromise, preventing additional attacks, or planning and executing system backup, incident response and data protection and recovery.
Define and implement a security awareness and training programme – because cybersecurity is a team sport, we’ll help you identify the specific knowledge, skills, and abilities that everyone in the organisation will need. That includes executing a plan to assess and remediate through policy, planning and awareness training.
Prepare a future roadmap – as your infosec requirements evolve, you’ll need to be able to ensure that every aspect of how you operate is covered and that every part of the organisation is protected. Whether that’s ensuring a secure configuration for all endpoints and assets or defining a password policy that’s in line with NCSC guidance. With dependencies expanding, users becoming more mobile, and an extraordinary array of security tools to choose from, we’ll help you.
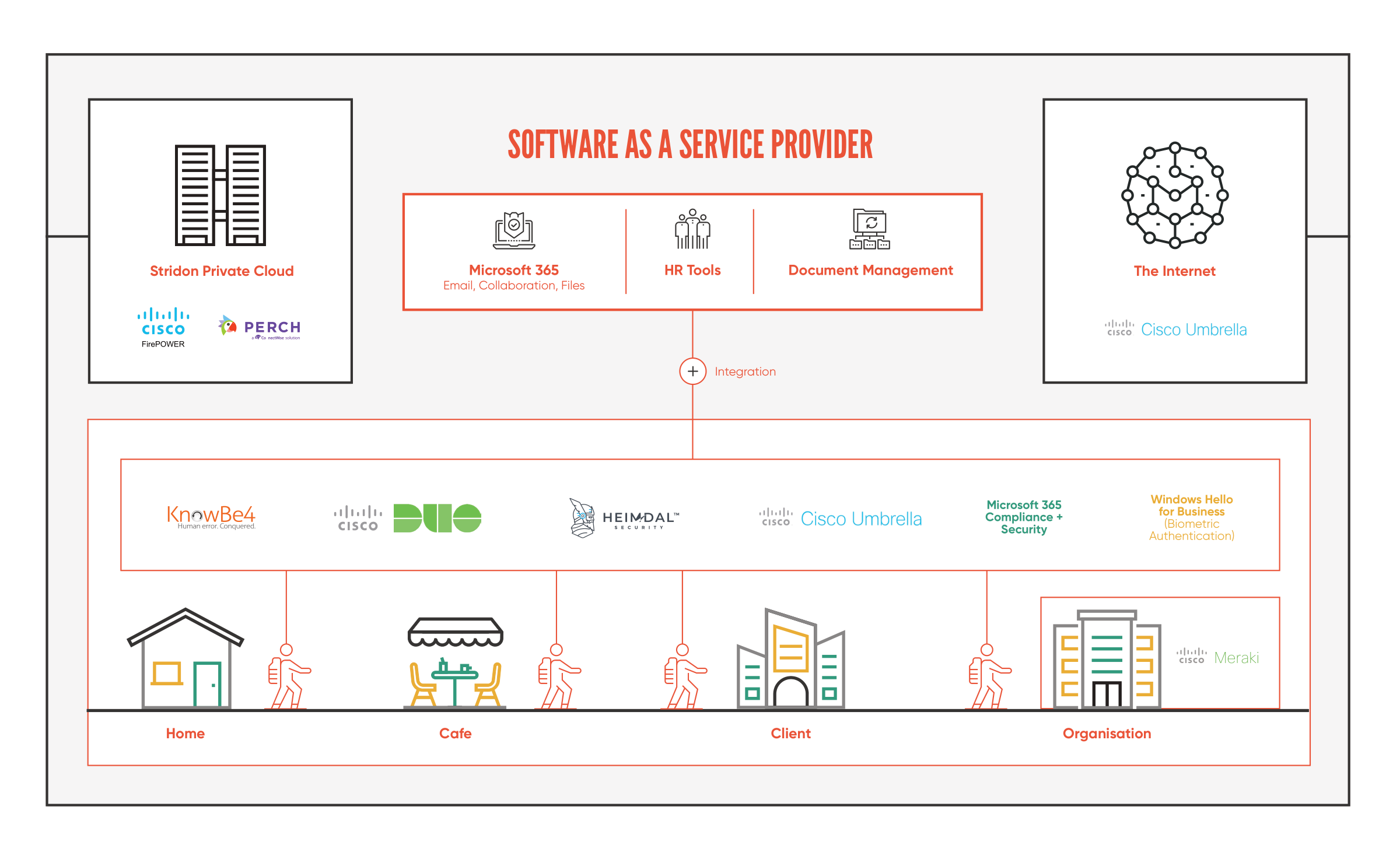
Combining the Right Tools
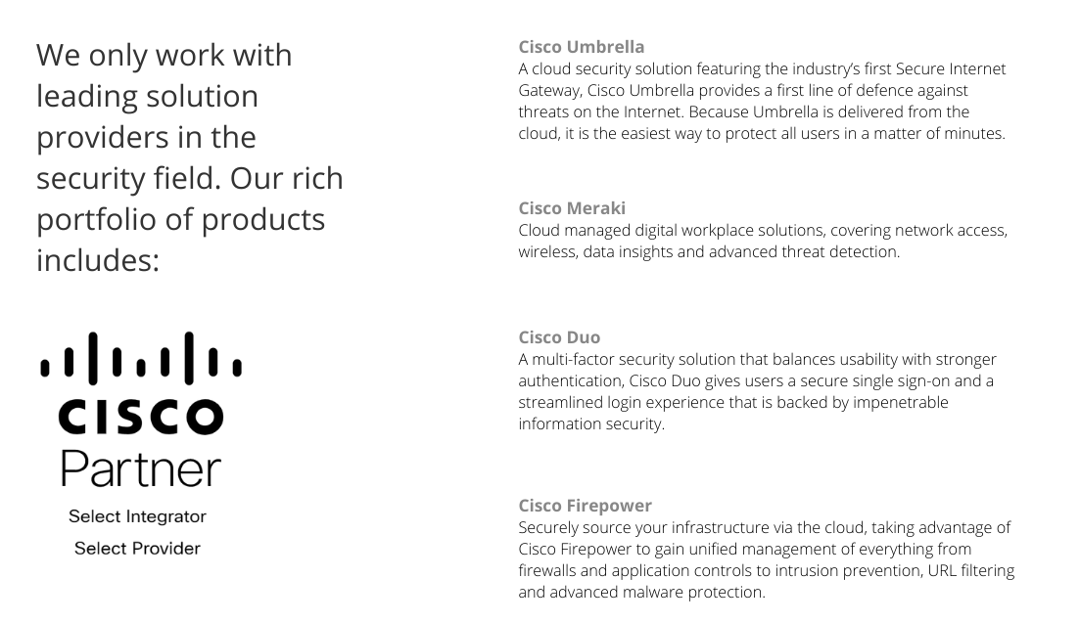
When it comes to analysing and improving your law firm’s data security, we’ll also combine a selection of solutions from leading vendors to ensure that every aspect of your operations is protected, and your top security priorities are addressed.
We don’t believe in a ‘one size fits all’ approach. Every law firm we work with must balance resource constraints with enabling risk mitigation that’s tailored to their unique activities and infrastructure environment. So, it’s vital to deploy the right combination of solutions that will both address organisation risk, and ensure compliance with regulatory responsibilities,
Deploying the right combination of solutions that’s appropriate for the operational model and maintains the confidentiality and integrity of sensitive data is just the start. Everything we select must integrate seamlessly with any existing security measures and deliver a reliable and scalable cyber defence systems that can be evolved in line with changing needs.

Let’s look at how we bring all these solutions together to protect a law firm that has people based in an office, is utilising Microsoft 365 delivered via the cloud – and has selected personnel who are working on a laptop in the comfort of their own home.